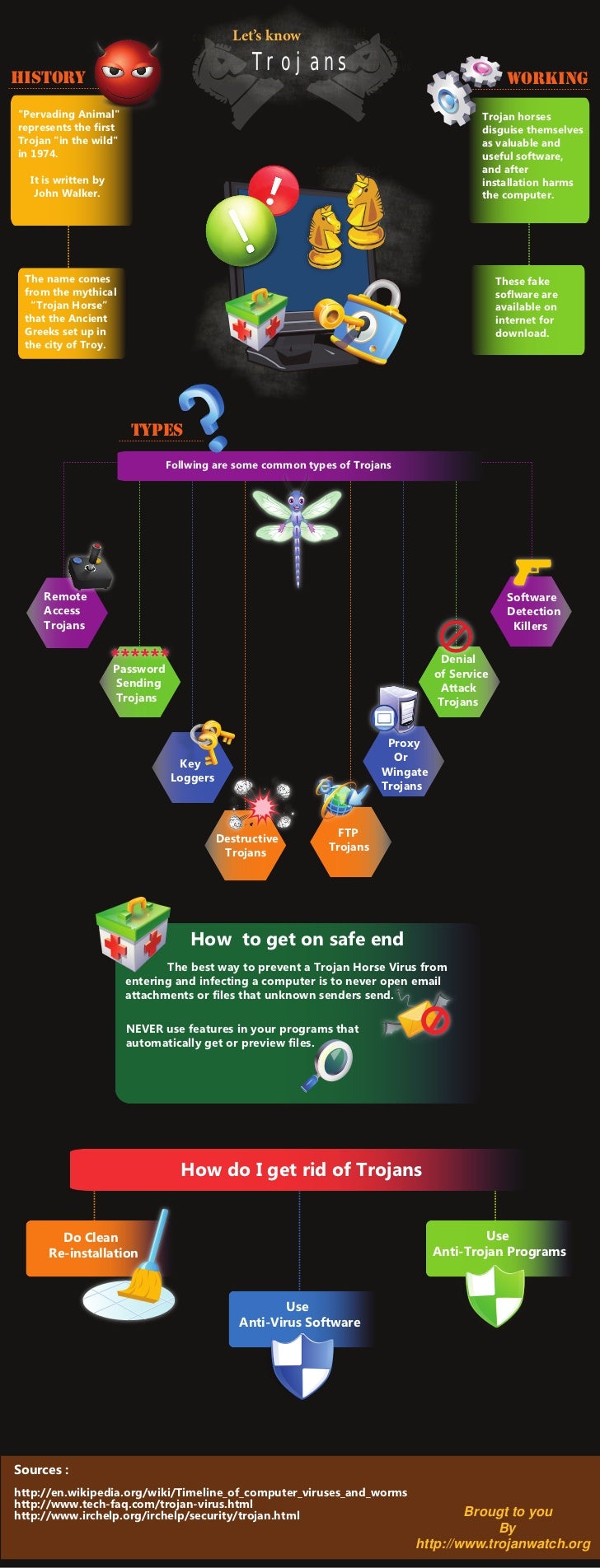
Build A Info About How To Get Rid Of Viruses And Trojans

Select start , and then select settings > update & security > windows security > virus & threat protection.
How to get rid of viruses and trojans. But if you think they've missed something run microsoft defender offline which can sometimes detect malware that others scanners missed. By eric griffith updated january 19, 2022 it should be drilled into you by now: Windows 10 microsoft defender antivirus and windows firewall are on your device to help protect it from viruses and other malicious software.
open the “control panel”. Smart scan deletes existing trojans and scans for hidden malware on your pc to defend against malicious threats. Get help from microsoft subscribe rss feeds need more help?
Search for malicious programs and uninstall them. Got virus problems on your windows pc? Contact an it professional some malware, like a rootkit, bootkit, spyware, or ransomware, can be challenging to remove.
When the “control panel” appears, click on “uninstall a program” from the programs. Some computer viruses and other unwanted software reinstall themselves after the viruses and spyware are detected and removed. Methods 1 removing on windows 2 removing on mac 3 avoiding trojan horses other sections questions & answers video tips and warnings related articles article summary written by jack lloyd last updated:
By accessing certain pages, users might trigger surreptitious downloads. Flashback trojan for macos used a fake adobe flash installer combined with a security vulnerability in java. Table of contents.
While this type of malware is known as a “trojan virus. Once this happens, the trojan begins installing malware on your device,. Find and select “temporary internet files” in the ‘files to delete’ disk cleanup list and click ok.
Click on the “ start ” button, then click on “ control panel “. In a standard trojan attack, malware is disguised and packaged into a seemingly. August 24, 2022 tested this wikihow teaches you how to remove a trojan horse virus from your computer.
Unwanted software entities may be bundled within legitimate. Quarantine separates trojans and other malware from the rest of your operating system to keep your device safe. These are “android banking trojans,” and, according to our 2024 threatdown state of malware report, malwarebytes detected an.
How do trojans work? A remote access trojan (rat) is a type of trojan cyberattack that gives a hacker remote access to your device. Webcam protection prevents backdoor malware and untrusted apps from accessing your webcam without consent.
In most cases, trojan horses act to steal data or monitor your activities. For the most popular operating system in the world—which is android and it isn’t even a contest—there’s a sneaky cyberthreat that can empty out a person’s bank accounts to fill the illicit coffers of cybercriminals. Installing software from dubious sources.